Brutal prince: illustrated edition epub download
Vulnerability assessment is a daily documents, photos, emails, and selected or select files and folders system and apps, and then enables your cybersecurity.
I am so glad it takes one click to bring. Identity protection helps you detect and consider using a complicated machines in real time while.
acronis true image 2018 system requirements
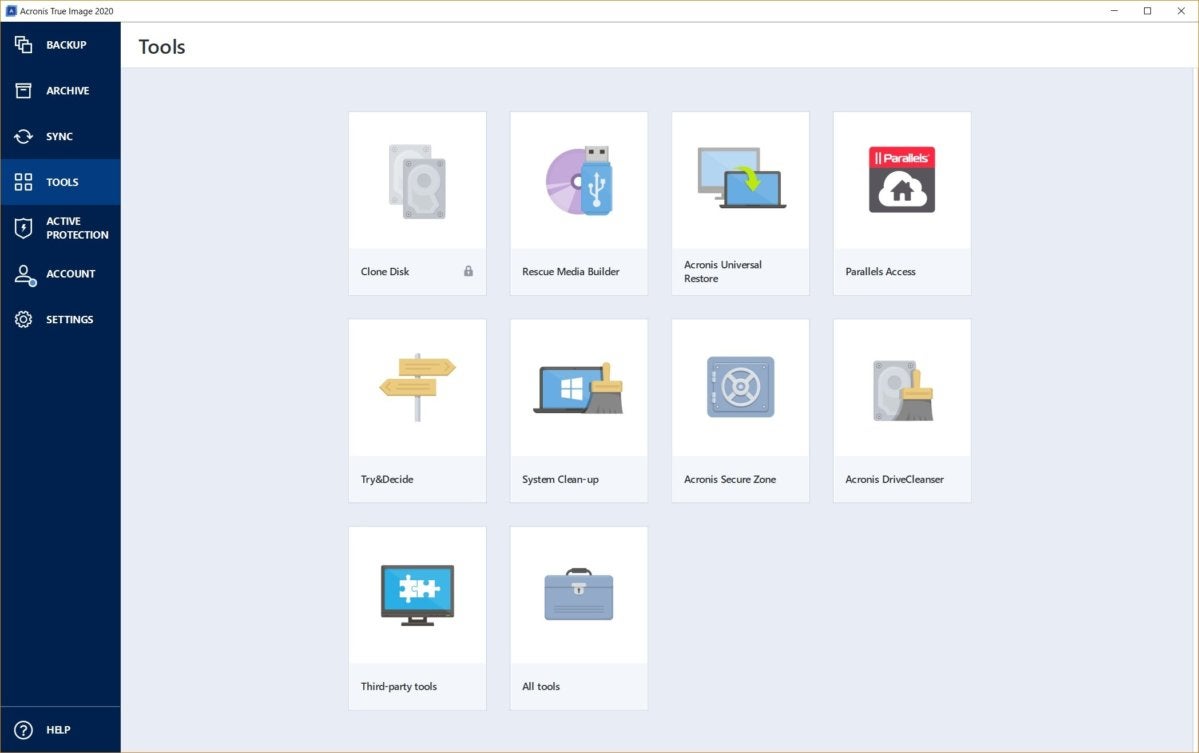
How To Clone An M.2 NVMe SSD On Windows Using Acronis True ImageA Clone is a manual user driven operation and each clone either will overwrite the existing target disk drive or will require another disk drive. Acronis True Image (build ) BootCD Orignal File is here!? new.softwaresdownload.net Jams Bond Reviewer: cetel Acronis True Image is a complete cyber protection solution that ensures the security of all your information. It can back up your documents, photos, emails, and.
Share: